As has been made abundantly clear by the advertising department of essentially every consumer electronics manufacturer on the planet: everything is improved by the addition of sensors and a smartphone companion app. Doesn’t matter if it’s your thermostat or your toilet, you absolutely must know at all times that it’s operating at peak efficiency. But why stop at household gadgets? What better to induct into the Internet of Things than 600 year old samurai weaponry?
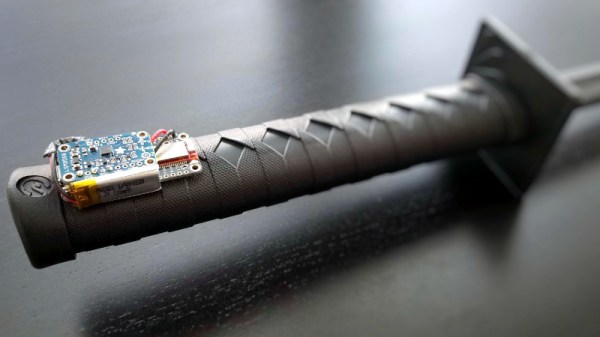
 Introducing the eKatana by [Carlos Justiniano]: by adding a microcontroller and accelerometer to the handle of a practice sword, it provides data on the motion of the blade as it’s swung. When accuracy and precision counts in competitive Katana exhibitions, a sword that can give you real time feedback on your performance could be a valuable training aid.
Introducing the eKatana by [Carlos Justiniano]: by adding a microcontroller and accelerometer to the handle of a practice sword, it provides data on the motion of the blade as it’s swung. When accuracy and precision counts in competitive Katana exhibitions, a sword that can give you real time feedback on your performance could be a valuable training aid.
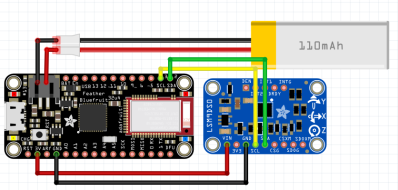
The eKatana is powered by an Adafruit Feather 32u4 Bluefruit LE and LSM9DS0 accelerometer module along with a tiny 110 mAh LiPo battery. Bundled together, it makes for a small and unobtrusive package at the base of the sword’s handle. [Carlos] mentions a 3D printed enclosure of some type would be a logical future improvement, though a practice sword that has a hollow handle to hold the electronics is probably the most ideal solution.
A real-time output of sword rotation, pitch, and heading is sent out by the Adafruit Feather over BLE for analysis by a companion smartphone application. For now he just has a running output of the raw data, but [Carlos] envisions a fully realized application that could provide the user with motions to perform and give feedback on their form.
Incidentally this isn’t the first motion-detecting sword we’ve ever covered, but we think this particular incarnation of the concept might have more practical applications.


 Over the years, a number of gadgets with BLE have popped up such as the LightBlue Bean, BLE Beacons as well as quadcopters like the FlexBot that rely on BLE for communication. Android or iOS apps are the predominant method of talking to these wonderful gadgets though there are alternatives.
Over the years, a number of gadgets with BLE have popped up such as the LightBlue Bean, BLE Beacons as well as quadcopters like the FlexBot that rely on BLE for communication. Android or iOS apps are the predominant method of talking to these wonderful gadgets though there are alternatives.