Friday, November 15, 2019 – PASADENA. The 2019 Hackaday Superconference is getting into high gear as I write this. Sitting in the Supplyframe HQ outside the registration desk is endlessly entertaining, as attendees pour in and get their swag bags and badges. It’s like watching a parade of luminaries from the hardware hacking world, and everyone looks like they came ready to work. The workshops are starting, the SMD soldering challenge is underway, and every nook and cranny seems to have someone hunched over the amazing Hackaday Superconference badge, trying to turn it into something even more amazing. The talks start on Saturday, and if you’re not one of the lucky hundreds here this weekend, make sure you tune into the livestream so you don’t miss any of the action.
The day when the average person is able to shoot something out of the sky with a laser is apparently here. Pablo, who lives in Argentina, has beeing keeping tabs on the mass protests going on in neighboring Chile. Huge crowds have been gathering regularly over the last few weeks to protest inequality. The crowd gathered in the capital city of Santiago on Wednesday night took issue with the sudden appearance of a police UAV overhead. In an impressive feat of cooperation, they trained 40 to 50 green laser pointers on the offending drone. The videos showing the green beams lancing through the air are quite amazing, and even more amazing is the fact that the drone was apparently downed by the lasers. Whether it was blinding the operator through the FPV camera or if the accumulated heat of dozens of lasers caused some kind of damage to the drone is hard to say, and we’d guess that the drone was not treated too kindly by the protestors when it landed in the midsts, so there’s likely not much left of the craft to do a forensic analysis, which is a pity. We will note that the protestors also trained their lasers on a police helicopter, an act that’s extremely dangerous to the human pilots which we can’t condone.
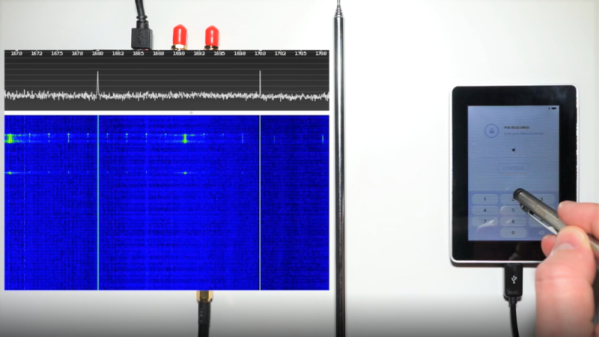
In news that should shock literally nobody, Chris Petrich reports that there’s a pretty good chance the DS18B20 temperature sensor chips you have in your parts bin are counterfeits. Almost all of the 500 sensors he purchased from two dozen vendors on eBay tested as fakes. His Github readme has an extensive list that lumps the counterfeits into four categories of fake-ness, with issues ranging from inaccurate temperature offsets to sensors without EEPROM that don’t work with parasitic power. What’s worse, a lot of the fakes test almost-sorta like authentic chips, meaning that they may work in your design, but that you’re clearly not getting what you paid for. The short story to telling real chips from the fakes is that Maxim chips have laser-etched markings, while the imposters sport printed numbers. If you need the real deal, Chris suggests sticking with reputable suppliers with validated supply chains. Caveat emptor.
A few weeks back we posted a link to the NXP Homebrew RF Design Challenge, which tasked participants to build something cool with NXP’s new LDMOS RF power transistors. The three winners of the challenge were just announced, and we’re proud to see that Razvan’s wonderfully engineered broadband RF power amp, which we recently featured, won second place. First place went to Jim Veatch for another broadband amp that can be built for $80 using an off-the-shelf CPU heatsink for thermal management. Third prize was awarded to a team lead by Weston Braun, which came up with a switch-mode RF amp for the plasma cavity for micro-thrusters for CubeSats, adorably named the Pocket Rocket. We’ve featured similar thrusters recently, and we’ll be doing a Hack Chat on the topic in December. Congratulations to the winners for their excellent designs.