After taking mental note of the number of surveillance cameras pointed at him while standing in line at the local Home Depot, [Mac Pierce] was inspired to create A Scanner Darkly. The art installation uses beams of light projected by mock security cameras to create a dot-matrix character display on the opposing wall, which slowly blinks out US surveillance laws and regulations.
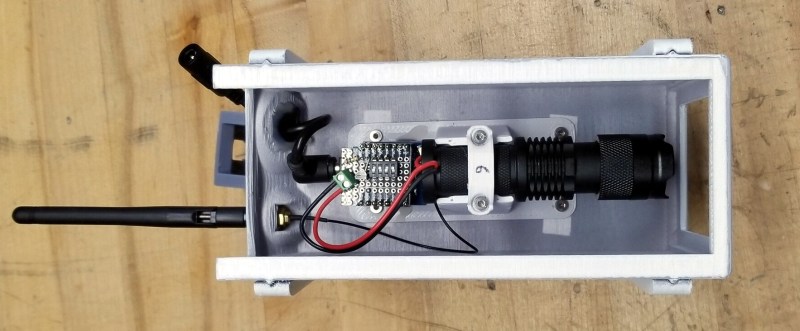
[Mac] has put together an extensive behind the scenes look at how he created A Scanner Darkly, which among other things covers the incredible time and effort that went into producing the fifteen identical cameras used to project the 3×5 grid. Early on he decided on 3D printing each one, as it would give him complete control over the final result. But given their considerable size, it ended up taking 230 hours and 12 kilograms of PLA filament to print out all the parts. It took a further 55 hours to sand and paint the camera housings, to make sure they didn’t actually look like they’d been 3D printed.
Internally, each camera has an off-the-shelf LED flashlight that’s had its power button rigged up to an ESP8266. Once they’ve been manually pointed to the appropriate spot on the wall, [Mac] can turn each camera’s spotlight on and off over WiFi. Rather than rely on the gallery’s infrastructure, all of the cameras connect to the ESP32 M5Stack that serves as the central controller via ESP-Now.
From there, it was just a matter of writing some code that would load a text document from the SD card, convert the current character into a 3×5 array, and then command the appropriate cameras to turn their lights on or off. [Mac] has not only provided the STL files for the 3D printed camera, but the client and server Arduino code to control the lights. Combined with his excellent documentation, this makes A Scanner Darkly something of a viral art piece; as anyone with the time and appropriate tools can either duplicate the installation or use it as a base for something new.
While some will no doubt argue that [Mac] could have completed this project far faster had he just modified some commercial dummy cameras, it’s important to remember that as an artist, he had a very specific look in mind for A Scanner Darkly. This project is a perfect example of how a creator’s passion can take an idea to new heights, and we think the end result proves it’s worth the time and sweat to put in the extra effort.
Continue reading “Building An Army Of Faux Cameras In The Name Of Art”