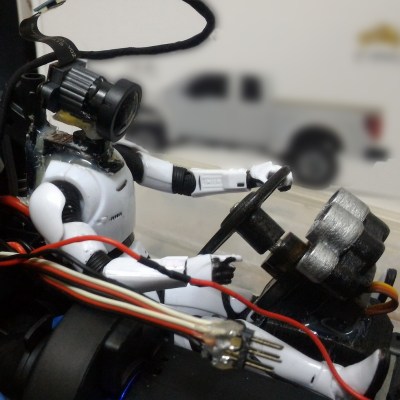
Pan and tilt mounts have a number of uses that can increase the functionality of various types of cameras. Security cameras can use them to adjust the field of view remotely, astronomers can use them as telescope mounts to accurately track celestial objects, and of course photographers and videographers can use them to add dynamic elements to shots. But getting the slow, smooth, and reliable movement isn’t as simple as slapping some servos on a tripod. So unless you want to break the bank for a commercial mount, this DIY pan and tilt mount might be the way to go.
The mount is built largely out of 3D printed parts and a few fairly common motors, belts, pulleys, and bearings. The movements are controlled using stepper motors, and there are two additional systems built in so that focus and zoom can be controlled through the system as well. The software controlling it all is open-source and available on GitHub, and controls the mount remotely through a network connection. It’s also designed to use the readily-available ESP32 chip, making it overall fairly adaptable.
The system doesn’t slouch on features, either. It can move from one point to another with various programmable speeds, has a key sequencer for more complex movements, and can accommodate the needs of stop motion animators as well. It’s an impressive build that should be accessible to plenty of photographers with a 3D printer and the right parts, but photography and astronomy aren’t the only reasons to use a pan and tilt mount. Check out this one that brings some sunlight to a shaded room.