[Usagi Electric] has his Centurion minicomputer (and a few others) running like a top. One feature that’s missing, though, is the ability to produce a hard copy. Now, a serious machine like the Centurion demands a serious printer. The answer to that is an ODEC-manufactured printer dressed in proper Centurion blue. This is no ordinary desktop printer, though. It’s a roughly 175lb (80 Kg) beast capable of printing 100 lines per minute. Each line is 132 characters wide, printed on the tractor-feed green bar paper we all associate with old computer systems.
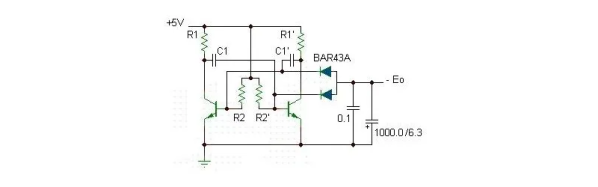
This sort of printer was commonly known as a chain printer, as the letters are on a chain that rides over a series of 66 hammers. Logic on this printer is 74 series logic chips – no custom silicon or LSI (Large Scale Integration) parts on this 47-year-old monster.
Continue reading “Bringing A Chain Printer Back To Life: The Power Supply”