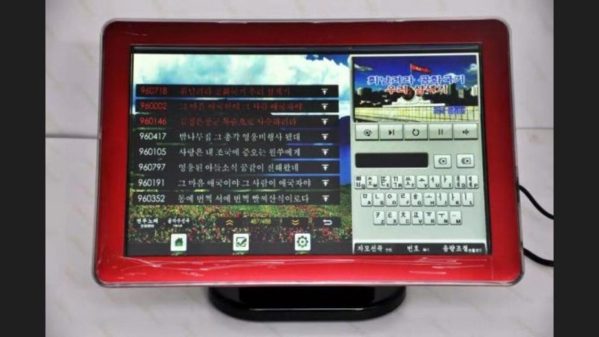
Karaoke is a very popular pastime in Seoul — there are venues where you can sing on a stage, sing in rooms with your friends, and even sing solo in coin-operated karaoke booths on the bullet train. Apparently it is also popular in North Korea as well — [Martyn Williams] of the North Korea Tech blog reported on an interesting teardown by web hacker [Will Scott]. It is the Tianchi v700 machine, a Chinese product tailored for North Korean users, obtained online back in 2020.
Unlike the karaoke machines encountered by this author in South Korea, the v700 form factor is a 19.5-inch Android tablet with touch-screen and all the necessary interfaces you’d expect: external video, speakers, and microphone, as well as WiFi and Ethernet for content upgrade and online payment systems. Not surprisingly, the connectivity aspects of the machine are not used in the North Korean model, but with a large catalog of pre-loaded music, it’s perfectly usable as a stand-alone device.
[Will] dug into the innards of the machine and discovered it was powered by an Allwinner ARM processor (seemingly the H6 V200, a quad-core ARM Cortex-A53). He also found it uses a swappable external disk to hold the songs, but all the files were encrypted. You can read more details in the blog post linked above, but eventually he was successful in decoding the disk and accessing the material.
The V700 consults both “/proc/cpuinfo” to learn the CPU serial number of the device it is on, and a binary file associated with the device file system structure as part of its method for determining its AES (Advanced Encryption Standard) key. It then ignores all of these device-specific items, and reverts back to a static key “87654321” stored in the binary.
All the songs on the disk were posted up on the Internet Archive. Check them out if you’re curious what North Korean karaoke songs sound and look like. One video that caught our attention was about CNC machines (see the video linked below the break). [Martyn] has been covering technology issues related to North Korea since 2011. In 2016, he learned after the fact that his website had been banned by the South Korean authorities. Believing this was in error, he appealed the ban and eventually prevailed in the courts. We wrote about some of [Will]’s research on consumer computing technology back in 2017 if you’re interested in learning more.
Continue reading “North Korean Karaoke Machine Teardown” →