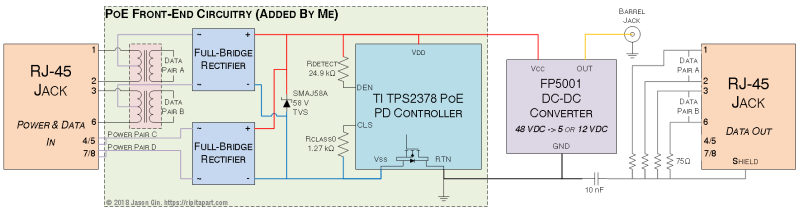
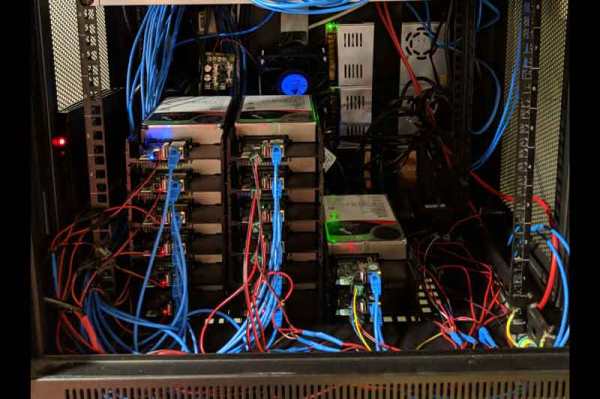
A NAS is always a handy addition to a home network, but they can be a little pricey. [Blake Burkhart] decided to create his own, prioritising budget and low power considerations, with a secondary objective to produce some router and IoT functionality on the side.
A Banana Pi R2 was a good choice to meet these requirements, being a router-based development board that also sports dual SATA connectors and gigabit Ethernet. [Blake] had some retrospective regrets about the performance of this particular SBC, but it does just fine when functioning purely as a NAS.
The enclosure for the device is a three bay hot-swap HDD module, with one of the bays gutted and used for the Banana Pi. It’s a simple idea, elegantly executed, which looks great. To access the ports of the Banana Pi, a custom acrylic side panel was laser cut, which also allowed LEDs to shine through – obligatory for any DIY server/computer build. When mounting this panel to the existing enclosure, [Blake] was reluctant to take his chances tapping the brittle acrylic, instead opting to melt the threads into the plastic with a pre-torched screw. We find that tapping acrylic is usually okay if you take it slow, but heat-tapping does sound fun.
The 12 V fan that came built into the hot-swap enclosure was too loud and awkwardly came in a non-standard size with a non-standard connector. What’s more, a buzzer alarm was triggered any time the fan was disconnected and 0 RPM was detected. [Blake]’s solution was to rewire the power pin of the connector to a 5 V rail; he found that running the fan at 5 V led to much quieter performance whilst keeping the HDDs sufficiently cool.
We find that when it comes to DIY network gear and routers, there are two approaches. Either create your own bespoke solution that perfectly fits your needs, like this perfect home router, or work around your current gear and build some tech to automatically reboot it for you.