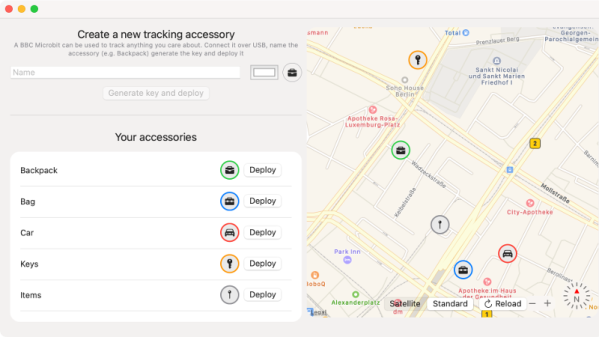
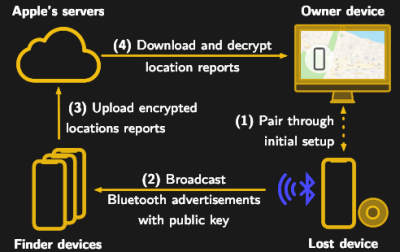
Apple’s “Find My” service allows users to track their missing devices by leveraging a worldwide network of location-aware iGadgets. With millions of iPhones and Macs out in the wild listening for the missing device’s Bluetooth advertisements and relaying their findings to the Cupertino Mothership, it’s a highly effective way of tracking hardware so long as it stays in relatively urban areas. Unfortunately, the system is completely proprietary and non-Apple devices aren’t invited to play.
Or at least, that used to be the case. A project recently released by the [Secure Mobile Networking Lab] called OpenHaystack demonstrates how generic devices can utilize Apple’s Find My network by mimicking the appropriate Bluetooth Low Energy (BLE) broadcasts. Currently they have a firmware image for the BBC micro:bit, as well as a Python script for Linux, that will allow you to spin up an impromptu Find My target. But the team has also published all the information required to implement similar functionality on other BLE-capable devices and microcontrollers, so expect the list of supported hardware to grow shortly.
 Somewhat ironically, while OpenHaystack allows you to track non-Apple devices on the Find Me tracking network, you will need a Mac computer to actually see where your device is. The team’s software requires a computer running macOS 11 (Big Sur) to run, and judging by the fact it integrates with Apple Mail to pull the tracking data through a private API, we’re going to assume this isn’t something that can easily be recreated in a platform-agnostic way. Beyond the occasional Hackintosh that might sneak in there, it looks like Tim Cook might have the last laugh after all.
Somewhat ironically, while OpenHaystack allows you to track non-Apple devices on the Find Me tracking network, you will need a Mac computer to actually see where your device is. The team’s software requires a computer running macOS 11 (Big Sur) to run, and judging by the fact it integrates with Apple Mail to pull the tracking data through a private API, we’re going to assume this isn’t something that can easily be recreated in a platform-agnostic way. Beyond the occasional Hackintosh that might sneak in there, it looks like Tim Cook might have the last laugh after all.
It’s not immediately clear how difficult it will be for Apple to close this loophole, but the talk of utilizing a private API makes us think there might be a built-in time limit on how long this project will be viable. After all, Big Tech doesn’t generally approve of us peons poking around inside their machinations for long. Though even if Apple finds a way to block OpenHaystack, it’s expected the company will be releasing “AirTags” sometime this year which will allow users to track whatever objects they like through the system.