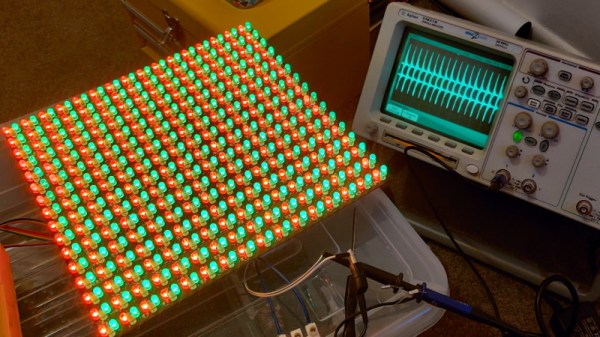
While out riding his bike, [Hammond Pearce] came across a dumpster overflowing with large LED panels. Despite the fact that the model numbers didn’t reveal anything helpful after some online searching, he decided to pedal off with as many as he could safely carry. The COVID-19 lockdown left him with only a limited set of tools, be he still managed to crack the protocol used to control his e-waste score and document it for our reading pleasure.
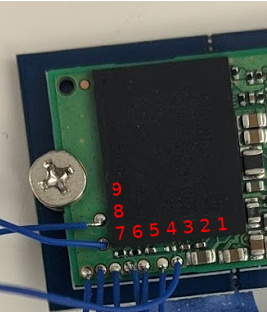
 Between the helpful labels on the PCB silkscreen and the advice of a friend that used to work on digital road signs, it didn’t take [Hammond] long to get a general idea of what the panels were looking for in terms of power and control. Especially once he noticed the MBI5024 shift registers dotting the board.
Between the helpful labels on the PCB silkscreen and the advice of a friend that used to work on digital road signs, it didn’t take [Hammond] long to get a general idea of what the panels were looking for in terms of power and control. Especially once he noticed the MBI5024 shift registers dotting the board.
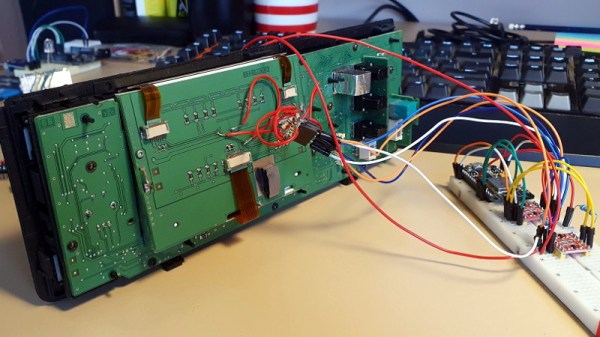
The next step was to take an ATmega328PB based development board and start throwing data at the panel’s input lines to see if he could elicit a response. With careful attention and some custom code, he eventually figured out that each byte of data sent down the line would control a 4 x 2 section of LEDs.
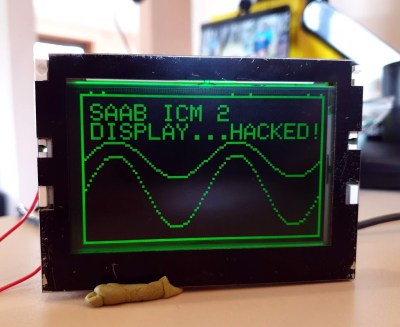
Once he had the basics down, the next step was to start expanding his code to handle things like shapes, text, and daisy-chained panels. After posting some of his work to Reddit, cyber-sleuths determined that the protocol appeared to be some variation of HUB75, which gave [Hammond] hints on what some of the other pins in the connector might be used for. He’s released all of his code online for anyone who might find it useful, but since he still doesn’t know who made these panels and why there’s really no telling how many of them are actually floating around out there.
Figuring out how to talk to an unknown or undocumented piece of hardware can be intimidating, but success stories like these are reminders of why it’s worth putting the effort in. As we’ve seen, the difference between trash and treasure is often a keen eye and a few lines of code.


 We might expect that the tool of choice would be a logic analyser or similar, but unexpectedly the solution to this hack was found in MAME. The arcade emulator conceals a wealth of information about these boards, from which you can discover their differences and try out possible solutions. The hardware hacks are surprisingly straightforward, a few bodge wires and an extra address line for a larger ROM. A programmable logic array required dumping and rewriting to fix a graphics corruption issue and a little bit of ROM tweaking after emulating a controller problem in MAME was required, but it seems that yes, one game can run on another. Certainly less painful than
We might expect that the tool of choice would be a logic analyser or similar, but unexpectedly the solution to this hack was found in MAME. The arcade emulator conceals a wealth of information about these boards, from which you can discover their differences and try out possible solutions. The hardware hacks are surprisingly straightforward, a few bodge wires and an extra address line for a larger ROM. A programmable logic array required dumping and rewriting to fix a graphics corruption issue and a little bit of ROM tweaking after emulating a controller problem in MAME was required, but it seems that yes, one game can run on another. Certainly less painful than