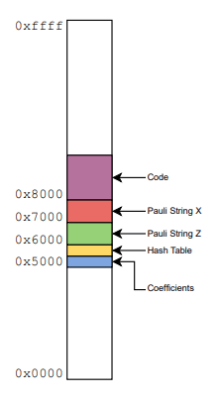
[MakerSpace] wanted to 3D print an RFID card holder. On one side is a slot for a card and on the other side has recesses for the RFID antenna. They used these to control access to machines and were milling them out using a CNC machine. Since there were no flat surfaces, he had to turn on supports in the slicer, right? No. He does use supports, but not in the way you might imagine.
Inspired by creating cast iron using sand casting, he decided to first 3D print a reusable “core” using PETG. This core will support future prints that use PLA. When printing the actual item, the printer lays down the first few layers and pauses. This allows you to stick the core in and resume the print. After the print completes, you can remove the core, and the results look great, as you can see in the video below.



![Sonic 2 on the Ti 84+ CE, courtesy of [grubbycoder]](https://hackaday.com/wp-content/uploads/2024/04/sonic_2_on_ti_84_ce.gif?w=320)