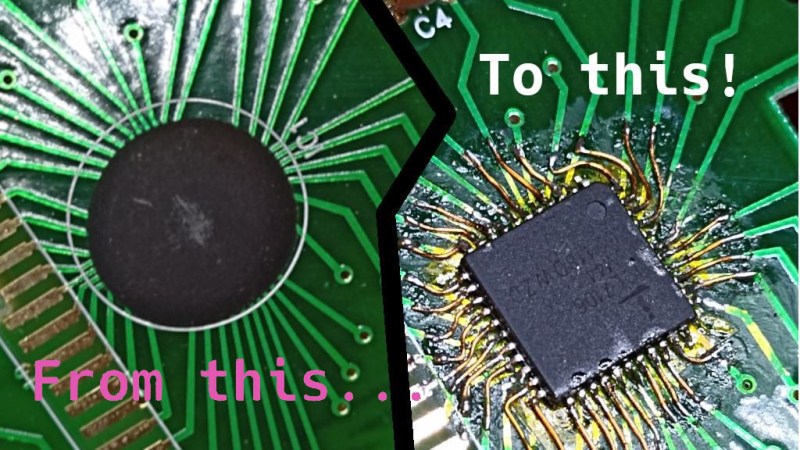
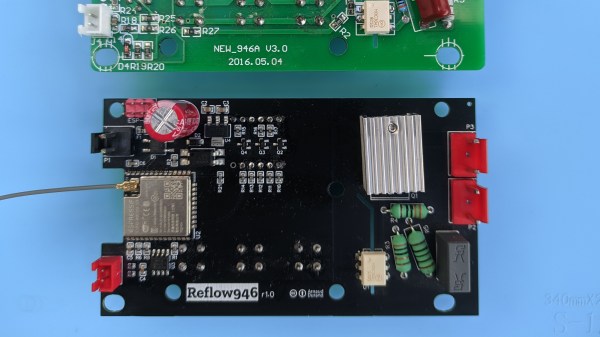
Reflow hotplates are a wonderful tool for PCB assembly if you can keep your designs single-sided. The 946C hotplate in particular has been on hackers’ radar for a while – a 200x200mm working surface hotplate available for under $100 is a decent investment. As with other reflow tools, it was a matter of time until someone made a replacement controller for it. This one, you’ll want to keep in mind – it’s a replacement controller project by [Arnaud Durand] and [Elias Rodriguez Martin], called Reflow946.
Keeping to best practices, the board is a drop-in replacement for the stock controller – swap cables over and go. The host processor is an ESP32, and it lets you can program reflow profiles in using BLE, with a Python application to help. The whole design is open-source and on GitHub, of course – keeping with best 3D printing traditions, you can already order the parts and PCBs, and then assemble them using the hotplate you’re about to upgrade. As far as aftermarket controllers go, here’s no doubt this board gives you way more control in reflow and lets you compensate for any possible subpar calibration while at it. Continue reading “Controller For 946C Hotplate Adds Reflow Profile Upload Over BLE”


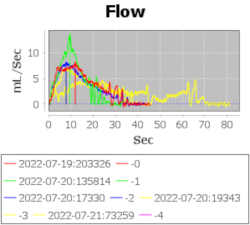 For the hardware, [Jerry] took a small digital scale of a certain model and reused its load cell-based weighing mechanism using an HX711 amplifier, replacing the screen and adding an extra box for control electronics. With an Arduino MKR1010 as brains of the operation, the hardware’s there to log flow data, initially recorded onto the SD card, with WiFi connectivity to transfer the data to a computer for plotting; a DS3234 RTC breakout helps keep track of the time, and a custom PCB ties all of these together. All of these things are easy to put together, in no small part due to the extensive instructions provided.
For the hardware, [Jerry] took a small digital scale of a certain model and reused its load cell-based weighing mechanism using an HX711 amplifier, replacing the screen and adding an extra box for control electronics. With an Arduino MKR1010 as brains of the operation, the hardware’s there to log flow data, initially recorded onto the SD card, with WiFi connectivity to transfer the data to a computer for plotting; a DS3234 RTC breakout helps keep track of the time, and a custom PCB ties all of these together. All of these things are easy to put together, in no small part due to the extensive instructions provided.