After covering a few of his builds at this point, we think it’s abundantly clear that [Igor Afanasyev] has a keen eye for turning random pieces of antiquated hardware into something that’s equal parts functional and gorgeous. He retains the aspects of the original which give it that unmistakable vintage look, while very slickly integrating modern components and features. His work is getting awfully close to becoming some kind of new art form, but we’re certainly not complaining.
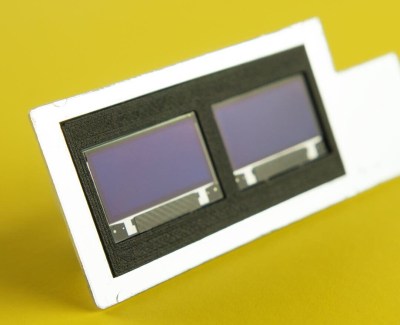 His latest creation takes an old-school “Monopak” electronic flash module and turns it into a desk clock that somehow also manages to look like a vintage television set. The OLED displays glowing behind the original flash diffuser create an awesome visual effect which really sells the whole look; as if the display is some hitherto undiscovered nixie variant.
His latest creation takes an old-school “Monopak” electronic flash module and turns it into a desk clock that somehow also manages to look like a vintage television set. The OLED displays glowing behind the original flash diffuser create an awesome visual effect which really sells the whole look; as if the display is some hitherto undiscovered nixie variant.
On the technical side of things, there’s really not much to this particular build. Utilizing two extremely common SSD1306 OLED displays in a 3D printed holder along with an Arduino to drive them, the electronics are quite simple. There’s a rotary encoder on the side to set the time, though it would have been nice to see an RTC module added into the mix for better accuracy. Or perhaps even switch over to the ESP8266 so the clock could update itself from the Internet. But on this build we get the impression [Igor] was more interested in playing with the aesthetics of the final piece than fiddling with the internals, which is hard to argue with when it looks this cool.
Noticing the flash had a sort of classic TV set feel to it, [Igor] took the time to 3D print some detail pieces which really complete the look. The feet on the bottom not only hold the clock at a comfortable viewing angle, but perfectly echo the retro-futuristic look of 50s and 60s consumer electronics. He even went through the trouble of printing a little antenna to fit into the top hot shoe, complete with a metal ring salvaged from a key-chain.
Late last year we were impressed with the effort [Igor] put into creating a retro Raspberry Pi terminal from a legitimate piece of 1970’s laboratory equipment, and more recently his modern take on the lowly cassette player got plenty of debate going. We can’t wait to see what he comes up with next.
Continue reading “Vintage Camera Flash Turned OLED Desk Clock”