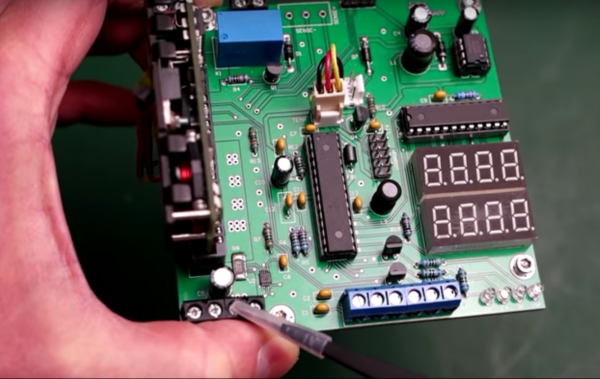
If you stuff a computer into a rack with a bunch of other machines, you’d better make it a tough machine. Server-grade means something, so using server parts in a project, like this high-wattage power supply using server voltage regulators, can take it to the next level of robustness.
But before [Andy Brown] could build this power supply, he had to reverse-engineer the modules. Based on what he learned, and armed with a data sheet for the modules, he designed a controller to take advantage of all the capabilities of them and ended up with a full-featured power supply. The modules are rated for 66 watts total dissipation at 3.3 volts and have a secondary 5-volt output. Using an ATmega328, [Andy] was able to control the module, provide a display for voltage and current, temperature sensing and fan control, and even a UART to allow data logging to a serial port. His design features mainly through-hole components to make the build accessible to everyone. A suitable case is yet to come, and we’re looking forward to seeing the finished product.
Can’t scrape together some of these modules on eBay? Or perhaps you prefer linear power supplies to switched- mode? No worries – here’s a super stable unregulated supply for you.
Continue reading “Bench Power Supply Uses Server Voltage Regulator”