Yik Yak is growing in popularity lately. If you are unfamiliar with Yik Yak, here’s the run down. It’s kind of like Twitter, but your messages are only shared with people who are currently within a few miles of you. Also, your account is supposed to be totally anonymous. When you combine anonymity and location, you get some interesting results. The app seems to be most popular in schools. The anonymity allows users to post their honest thoughts without fear of scrutiny.
[Sanford Moskowitz] decided to do some digging into Yik Yak’s authentication system. He wanted to see just how secure this “anonymous” app really is. As it turns out, not as much as one would hope. The primary vulnerability is that Yik Yak authenticates users based solely on a user ID. There are no passwords. If you know the user’s ID number, it’s game over.
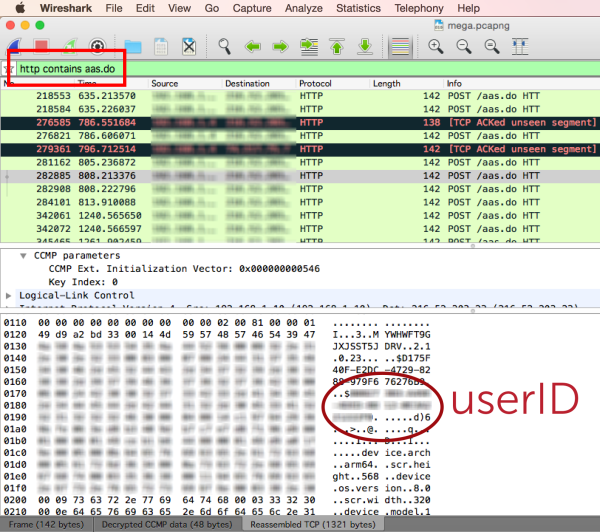
The first thing [Sanford] looked for was an encrypted connection to try to sniff out User ID’s. It turned out that Yik Yak does actually encrypt the connection to its own servers, at least for the iPhone app. Not to worry, mobile apps always connect to other services for things like ad networks, user tracking, etc. Yik Yak happens to make a call to an analytics tool called Flurry every time the app is fired. Flurry needs a way to track the users for Yik Yak, so of course the Yik Yak App tells Flurry the user’s ID. What other information would the anonymous app have to send?
Unfortunately, Flurry disables HTTPS by default, so this initial communication is in plain text. That means that even though Yik Yak’s own communications are protected, the User ID is still exposed and vulnerable. [Sanford] has published a shell script to make it easy to sniff out these user ID’s if you are on the same network as the user.
Once you have the user ID, you can take complete control over the account. [Sanford] has also published scripts to make this part simple. The scripts will allow you to print out every single message a user has posted. He also describes a method to alter the Yik Yak installation on a rooted iPhone so that the app runs under the victim’s user ID. This gives you full access as if you owned the account yourself.
Oh, there’s another problem too. The Android app is programmed to ignore bad SSL certificates. This means that any script kiddie can perform a simple man in the middle attack with a fake SSL certificate and the app will still function. It doesn’t even throw a warning to the user. This just allows for another method to steal a user ID.
So now you have control over some poor user’s account but at least they are still anonymous, right? That depends. The Yik Yak app itself appears to keep anonymity, but by analyzing the traffic coming from the client IP address can make it trivial to identify a person. First of all, [Sanford] mentions that a host name can be a dead giveaway. A host named “Joe’s iPhone” might be a pretty big clue. Other than that, looking out for user names and information from other unencrypted sites is easy enough, and that would likely give you everything you need to identify someone. Keep this in mind the next time you post something “anonymously” to the Internet.
[via Reddit]