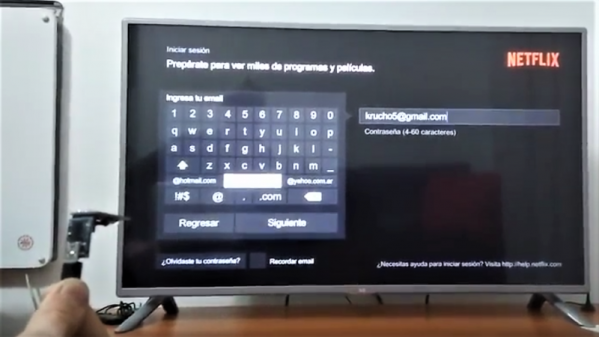
Who would have thought that you could light up pyrotechnics on USB power? This USB keystroke injector that blows up after it’s used proves the concept.
Fully aware that this is one of those “just because you can doesn’t mean you should” projects, [MG] takes pains to point out that his danger dongle is just for dramatic effect, like a prop for a movie or the stage. In fact, he purposely withholds details on the pyrotechnics and concentrates on the keystroke injection aspect, potentially nasty enough by itself, as well as the dongle’s universal payload launching features. We’re a little bummed, because the confetti explosion (spoiler!) was pretty neat.
The device is just an ATtiny85 and a few passives stuffed into an old USB drive shell, along with a MOSFET to trigger the payload. If you eschew the explosives, the payload could be anything that will fit in the case. [MG] suggests that if you want to prank someone, an obnoxious siren might be a better way to teach your mark a lesson about plugging in strange USB drives.
While this isn’t the most dangerous thing you can do with a USB port, it could be right up there with that rash of USB killer dongles from a year or so ago. All of these devices are fun “what ifs”, but using them on anything but your own computers is not cool and possibly dangerous. Watching the smoke pour out of a USB socket definitely drives home the point that you shouldn’t plug in that thumbdrive that you found in the bathroom at work, though.
Continue reading “This USB Drive Will Self-Destruct After Ruining Your Computer”


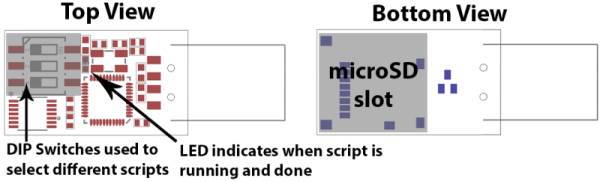


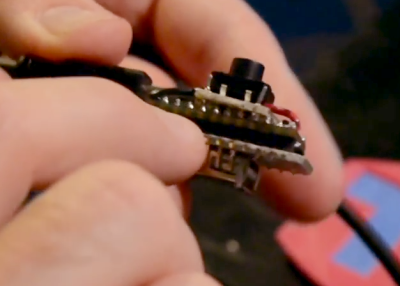 The idea started with the concept of a dedicated device to carry a complicated password; something that you couldn’t remember yourself and would be difficult to type. [Dan] also decided it would be much better if the device didn’t need its own power source, and if the user interface was dead simple. The answer was a wrist-band made up of a USB cable and a microcontroller with just one button.
The idea started with the concept of a dedicated device to carry a complicated password; something that you couldn’t remember yourself and would be difficult to type. [Dan] also decided it would be much better if the device didn’t need its own power source, and if the user interface was dead simple. The answer was a wrist-band made up of a USB cable and a microcontroller with just one button. [Dan] came up with the idea to have a pair of mating boards for the Teensy 2.0. One on top hosts the button, the other on the bottom has a USB port which is used as the “clasp” of the belt buckle. One side of the USB cable plugs into the Teensy, the other into this dummy-port. Early testing showed that this was too bulky to work as a bracelet. But [Dan] simply pivoted and turned it into a belt.
[Dan] came up with the idea to have a pair of mating boards for the Teensy 2.0. One on top hosts the button, the other on the bottom has a USB port which is used as the “clasp” of the belt buckle. One side of the USB cable plugs into the Teensy, the other into this dummy-port. Early testing showed that this was too bulky to work as a bracelet. But [Dan] simply pivoted and turned it into a belt. [Kenji Larsen] helped [Dan] with the PCB-sandwich. Instead of mounting pin sockets on the extra boards, they heated up the solder joints on a few of the Teensy pins and pushed them through with some pliers. This left a few pins sticking up above the board to which the button add-on board could be soldered.
[Kenji Larsen] helped [Dan] with the PCB-sandwich. Instead of mounting pin sockets on the extra boards, they heated up the solder joints on a few of the Teensy pins and pushed them through with some pliers. This left a few pins sticking up above the board to which the button add-on board could be soldered.













