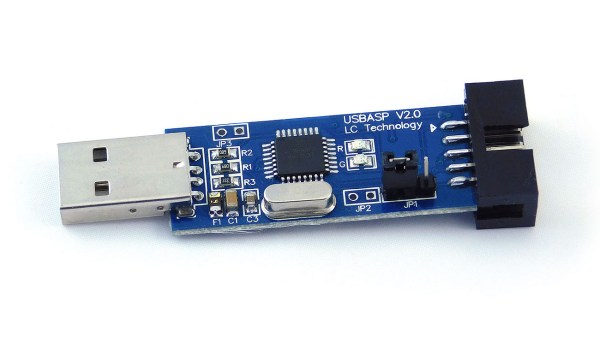
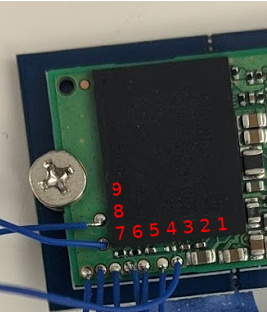
Last Fall [Kevin] wanted to program some newer TPI-only AVRs using an old USBasp he had kicking around his lab. Finding an “odd famine of information” and “forums filled with incorrect information and schematics”, he decided to set the record straight and document things correctly. He sleuthed out the details and succeeded in reprogramming the USBasp, although he did end up buying a second one in the process.
Designers who use AVR microcontrollers have no shortage of programming interfaces — we count at least five different methods: ISP/SPI, JTAG, TPI, PDI, and UPDI. We’re not sure whether this is variety is good or bad, but it is what it is. [Kevin] discovers that for the particular family of Attiny devices he is using, the ATtiny20, TPI is the only option available.
While he normally builds his designs around ARM Cortex-M chips, [Kevin] needed some glue logic and decided to go with an ATtiny20 despite its unique programming requirements. He observes that the price of the ATtiny20, $0.53 last Fall, was cheaper than the equivalent logic gates he needed. This particular chip is also quite small — only 3 mm square (a 20-pin VQFN). We would prefer not to use different MCUs and tool chains on a single board, but sometimes the convenience and economics steer the design in that direction.
If you’re not familiar with the USBasp, our own [Mike Szczys] covered the breaking story over ten years ago. And if you have a lot of free time on your hands, ditch all these nicely packaged solutions and program your chips using an old USB Hub and a 74HCT00 NAND gate as described in this bizarre hack by Teensy developer [Paul Stoffregen].