[Nikhil] has been experimenting with human interface devices (HID) in relation to security. We’ve seen in the past how HID can be exploited using inexpensive equipment. [Nikhil] has built his own simple device to drop malicious files onto target computers using HID technology.
The system runs on a Teensy 3.0. The Teensy is like a very small version of Arduino that has built-in functionality for emulating human interface devices, such as keyboards. This means that you can trick a computer into believing the Teensy is a keyboard. The computer will treat it as such, and the Teensy can enter keystrokes into the computer as though it were a human typing them. You can see how this might be a security problem.
[Nikhil’s] device uses a very simple trick to install files on a target machine. It simply opens up Powershell and runs a one-liner command. Generally, this commend will create a file based on input received from a web site controlled by the attacker. The script might download a trojan virus, or it might create a shortcut on the user’s desktop which will run a malicious script. The device can also create hot keys that will run a specific script every time the user presses that key.
Protecting from this type off attack can be difficult. Your primary option would be to strictly control USB devices, but this can be difficult to manage, especially in large organizations. Web filtering would also help in this specific case, since the attack relies on downloading files from the web. Your best bet might be to train users to not plug in any old USB device they find lying around. Regardless of the methodology, it’s important to know that this stuff is out there in the wild.





 A couple of years ago he worked on a standalone chemical sensor and had a few extra boards sitting around after the project was done. As any resourceful hacker will do, he reached for them as the closest and easiest solution when needing to log data as a quick test. It wasn’t for quite some time that he went back to try out commercially available loggers and found a problem in doing so.
A couple of years ago he worked on a standalone chemical sensor and had a few extra boards sitting around after the project was done. As any resourceful hacker will do, he reached for them as the closest and easiest solution when needing to log data as a quick test. It wasn’t for quite some time that he went back to try out commercially available loggers and found a problem in doing so.
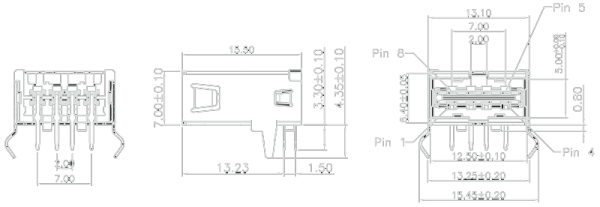
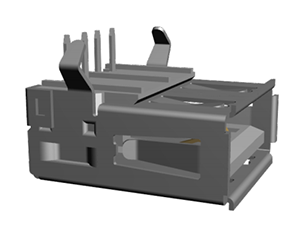 The connector isn’t the brand new USB 3.1 Type C connector that will eventually find its way into phones, laptops, wearables of all types. This is your standard Type A USB plug you’ve known and loved for the past eighteen years. The difference here is that the chunky block of plastic that has made the common USB cable non-reversible for so many years is gone. In its place is a tiny strip of plastic that has contacts on both sides. Yes, it took nearly two decades for someone to figure out this would be a marketable idea.
The connector isn’t the brand new USB 3.1 Type C connector that will eventually find its way into phones, laptops, wearables of all types. This is your standard Type A USB plug you’ve known and loved for the past eighteen years. The difference here is that the chunky block of plastic that has made the common USB cable non-reversible for so many years is gone. In its place is a tiny strip of plastic that has contacts on both sides. Yes, it took nearly two decades for someone to figure out this would be a marketable idea.









