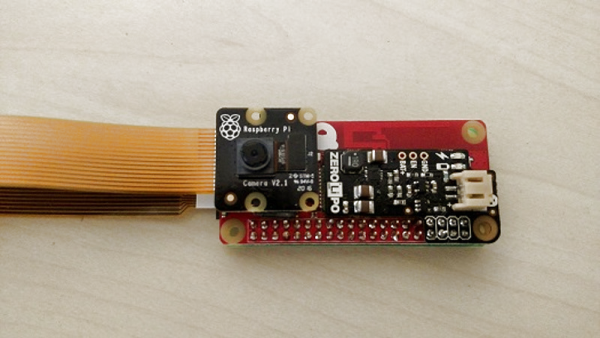
What makes [mwagner1]’s Raspberry Pi Zero-based WiFi camera project noteworthy isn’t so much the fact that he’s used the hardware to make a streaming camera, but that he’s taken care to document every step in the process from soldering to software installation. Having everything in one place makes it easier for curious hobbyists to get those Pi units out of a drawer and into a project. In fact, with the release of the Pi Zero W, [mwagner1]’s guide has become even simpler since the Pi Zero W now includes WiFi.
Using a Raspberry Pi as the basis for a WiFi camera isn’t new, but it is a project that combines many different areas of knowledge that can be easy for more experienced people to take for granted. That’s what makes it a good candidate for a step-by-step guide; a hobbyist looking to use their Pi Zero in a project may have incomplete knowledge of any number of the different elements involved in embedding a Pi such as basic soldering, how to provide appropriate battery power, or how to install and configure the required software. [mwagner1] plans to use the camera as part of a home security system, so stay tuned.
If Pi Zero camera projects catch your interest but you want something more involved, be sure to check out the PolaPi project for a fun, well-designed take on a Pi Zero based Polaroid-inspired camera.