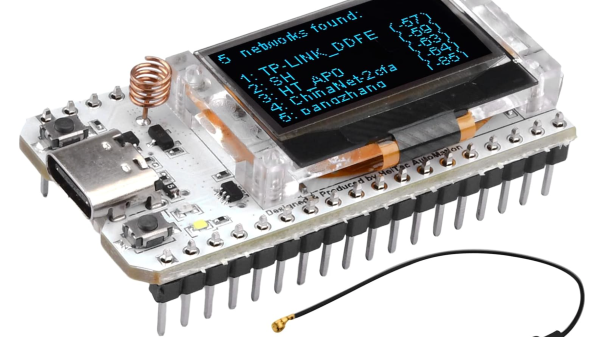
The range of hardware that comes on some dev boards these days is truly staggering. Those little LoRa boards are a prime example — ESP32 with WiFi and Bluetooth, a transceiver that covers a big chunk of the UHF band, and niceties like OLED displays and plenty of GPIO. But the firmware and docs? Well, if you can’t say something nice, don’t say anything at all. Or better yet, just roll your own.
Of course that doesn’t hold true for all the LoRa dev boards on the market, but [Rop] certainly found it to be the case for the Heltec HTIT-WB32LA. This board has all the bells and whistles and would be perfect for LoraWAN and Meshtastic applications, but it needed a little help getting it over the line. [Rop]’s contribution to this end is pretty comprehensive and is based on his fork of the RadioLib library, which incorporates a library that greatly reduces wear on the ESP32’s flash memory. In addition to full radio support, the library supports all the hardware on the board from the pushbutton to the display, power management and battery charging, and of course the blinkenlights.
[Jop] includes quite a few example applications, from the bare minimum needed to get the board spun up to a full-blown spectrum analyzer. It’s a nice piece of work, and a great give-back to the LoRa community. And if you want to put one of these modules to work, you’re certainly in the right place. We’ve got everything from LoRaWAN networks to the magic of Meshtastic, so take your pick and get hacking.