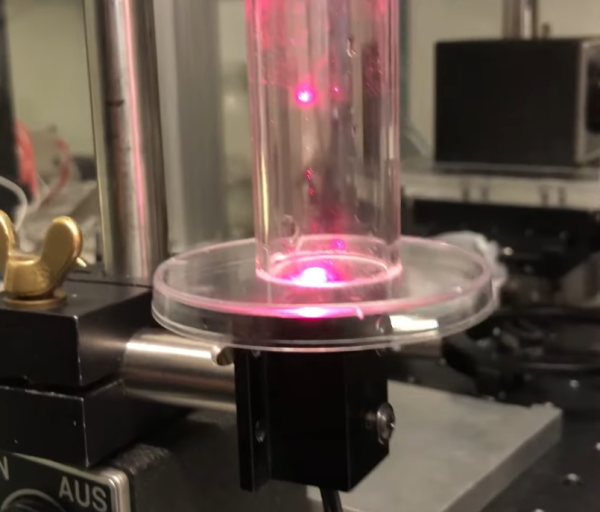
No matter how small you make a pair of tweezers, there will always be things that tweezers aren’t great at handling. Among those are various fluids, and especially aerosolized droplets, which can’t be easily picked apart and examined by a blunt tool like tweezers. For that you’ll want to reach for a specialized tool like this laser-based tool which can illuminate and manipulate tiny droplets and other particles.
[Janis]’s optical tweezers use both a 170 milliwatt laser from a DVD burner and a second, more powerful half-watt blue laser. Using these lasers a mist of fine particles, in this case glycerol, can be investigated for particle size among other physical characteristics. First, he looks for a location in a test tube where movement of the particles from convective heating the chimney effect is minimized. Once a favorable location is found, a specific particle can be trapped by the laser and will exhibit diffraction rings, or a scattering of the laser light in a specific way which can provide more information about the trapped particle.
Admittedly this is a niche tool that might not get a lot of attention outside of certain interests but for those working with proteins, individual molecules, measuring and studying cells, or, like this project, investigating colloidal particles it can be indispensable. It’s also interesting how one can be built largely from used optical drives, like this laser engraver that uses more than just the laser, or even this scanning laser microscope.
Continue reading “Optical Tweezers Investigate Tiny Particles”