With three kids, including himself, [Dave] faced the very real likelihood of someone absent-mindedly leaving the garage door open and being robbed blind. Rather than installing some plebeian solution, he compiled a feature list. And what a feature list it is!
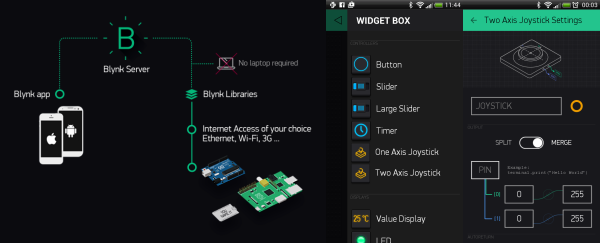
The garage door needed to notify him of its status with strategically placed LEDs around the house, and give him full control on his devices. He wanted to open and close it using his existing key-code entry system. Lastly, it would be extra-cool if he could add some biometrics to it; in this case, a fingerprint sensor.
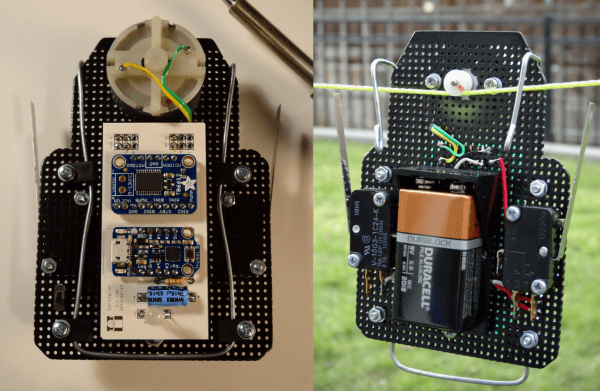
The core hardware is the staple Arduino augmented with a fingerprint module, a touch screen, some vitamins, and a WiFi break-out. He also worked up some casings in tinkercad: one for the indoor hardware, another with a flip cover for the outdoor fingerprint scanner.
We think [Dave] has accomplished what he set out to. We can just picture the would-be-thief staring at the finger print scanner and moving their operation one house over where the world is simpler. Video after the break.
Continue reading “Fingerprint Garage Door Won’t Open Every Time A Neighbor Microwaves A Burrito”