You might be surprised to find out that it’s actually not a good idea to put all of your credit card information on a little Bluetooth enabled device in your pocket. Oh, what’s that? You knew already? Well in that case you won’t find the following information terribly shocking, but it’s still a fascinating look at how security researchers systematically break down a device in an effort to find the chinks in its armor.
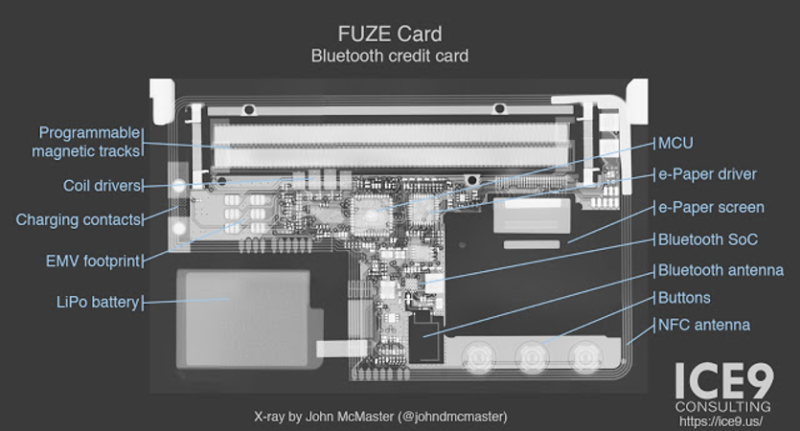 [Mike Ryan] of ICE9 Consulting has recently published an article detailing the work done to examine and ultimately defeat the security on the FUZE Card. From using an x-ray machine to do non-destructive reconnaissance on the device’s internals to methodically discovering all the commands it responds to over Bluetooth, it’s safe to say the FUZE Card is cracked wide open at this point.
[Mike Ryan] of ICE9 Consulting has recently published an article detailing the work done to examine and ultimately defeat the security on the FUZE Card. From using an x-ray machine to do non-destructive reconnaissance on the device’s internals to methodically discovering all the commands it responds to over Bluetooth, it’s safe to say the FUZE Card is cracked wide open at this point.
To be clear, the attacker must still pair with FUZE, so physical access is required. But as pointed out by [Mike] in the blog post, handing your card over to a merchant is standard operating procedure in many cases. It isn’t as if it would be hard to get a hold of one of these FUZE cards for a minute or two without the owner becoming suspicious. Pairing FUZE to the Linux device to continue to the next step of the attack only takes a few seconds, as demonstrated in the video after the break.
Once paired, the attacker can simply send a BLE command to FUZE which disables the lock screen. It’s really that simple. The attacker can also send commands to dump credit card info over Bluetooth, meaning they could download your information even when the card is “safely” back in your pocket. The inherent failure in the FUZE design is that you don’t need to provide any sort of authentication to pair it to a new Bluetooth device. It makes the (very dangerous) assumption that the person holding it is entitled to do so.
Even if you know better than to ever buy a device like this, the post [Mike] has written up is really a must-read for anyone who’s ever looked at a device and tried to figure out what was going on in its little silicon brain. We especially liked his assertion that reverse engineering a device essentially boils down to: “staring, thinking, a little experimentation, but mostly staring and thinking.” We’re having an internal debate here at Hackaday HQ about making that the site’s tagline.
Incidentally, this is very similar to the Bluetooth gun “safe” that was cracked not so long ago. At this point, it might be wise to just stay away from anything with that little blue logo on it if you intend to trust it with your identity and/or deadly weapon.