For better or worse, most drivers for PC-related hardware like RGB components and fan controllers are built for Windows and aren’t generally of the highest quality. They’re often proprietary and clunky, and even if they aren’t a total mess they generally won’t work on Linux machines at all, or even on a headless setup regardless of OS. This custom fan controller, on the other hand, eschews the operating system almost entirely in favor of an open source fan controller board that can be reached over a network instead.
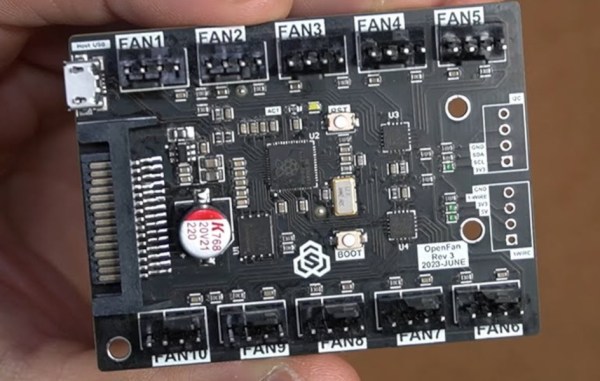
The project’s creator, [Sasa Karanovic], experimented with fan splitters to solve his problems, but found that these wouldn’t be the ideal solution given the sheer number of fans he wanted in his various computers, especially in his network-attached storage machine. For that one he wanted ten fans, with control over them in custom groups that would behave in certain ways depending on what the computer was doing. His solution uses two EMC2305 five-fan controller chip which communicates over I2C on a custom PCB with a RP2040 at the center. This allows the hardware to communicate with USB to the host computer for updating firmware and controlling over the network. There’s also a 1-wire and I2C bus exposed in case any external sensors need to be integrated into this system as well. To get power for all of those fans, the board uses a SATA connector to get power from the computer’s power supply.
With the PCB built and all of the connections to the host computer made, the custom board is able to control up to 10 fans in any custom configuration without needing a monitor or a driver since it is accessible over the network through an API. It’s also open-source so any changes to the firmware or hardware can easily be made for most air-cooled PC situations. If you’re less concerned about the internal case temperature and more concerned about all the heat your PC is dumping into a living space, you might want to look into venting your PC outside instead.
Continue reading “PC Fan Controller Works On Most Operating Systems”