The Internet has allowed us to communicate more easily than ever before, and thanks to modern cell-phone networks, we don’t even have to be tied down to a hard line anymore. But what if you want something a little more direct? Maybe you’re in an area with no cell-phone coverage, or you don’t want to use public networks for whatever reason. For those cases, you might be interested in this Secure Communication Network project by [Thomas].
By leveraging the plug-and-play qualities of the Raspberry Pi 4 and the Adafruit LoRa Radio Bonnet, [Thomas] has been able to focus on the software side of this system that really turns these parts into something useful.
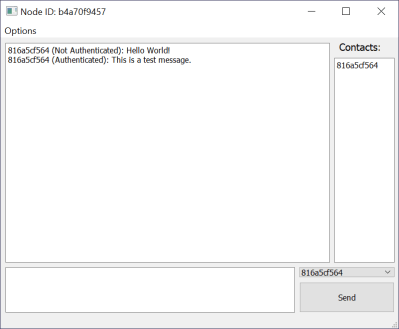
Rather than a simple point-to-point radio link, a mesh network is built up of any transceivers in range, extending the maximum distance a message can be sent, and building in resilience in case a node goes down. Each node is connected to a PC via Ethernet, and messages are distributed via a “controlled flooding” algorithm that aims to reduce unnecessary network congestion from the blind re-transmission of messages that have already been received.
Security is handled via RSA encryption with 256-byte public/private keys and additional SHA256 hashes for authentication.
The packet-size available through the LoRa device is limited to 256 bytes, of which 80 bytes are reserved for headers. To make matters worse, the remaining 176 bytes must contain encrypted data, which is almost always more lengthy than the raw message it represents. Because of this, longer messages are fragmented by the software, with the fragments sent out individually and re-assembled at the receiving end.
If you’re in need of a decentralized secure radio communications system, then there’s a lot to like about the project that [Thomas] has documented on his Hackaday.io page. He even includes an STL file for a 3D printed case. If you need to send more than text, then this Voice-over-LoRa Mesh Network project may be more your style.




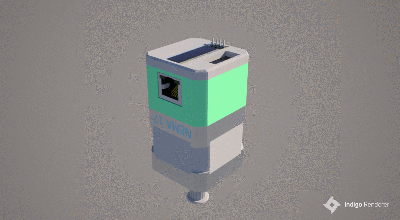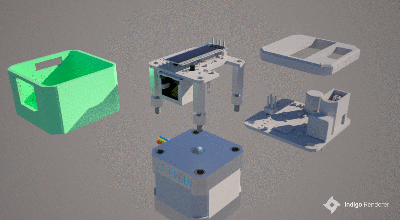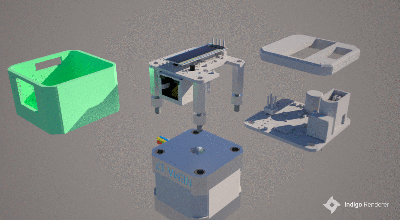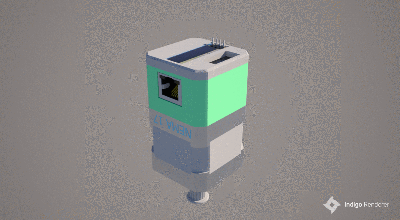 making uploading firmware a breeze. To that end, a USB port is also provided, hooked up to the uC with the cheap CP2102 USB bridge chip as per most Arduino-like designs. The thing that makes this build a little unusual is the ethernet port. The hardware side of things is taken care of with the
making uploading firmware a breeze. To that end, a USB port is also provided, hooked up to the uC with the cheap CP2102 USB bridge chip as per most Arduino-like designs. The thing that makes this build a little unusual is the ethernet port. The hardware side of things is taken care of with the