Really, how did we get the point in this world where an exercise bike can be bricked? Such was the pickle that [ptx2] was in when their $2,000 bike by Flywheel Home Sports was left without the essential feature of participating in virtual rides after Peloton bought the company. The solution? Reverse engineer the bike to get it working with another online cycling simulator.
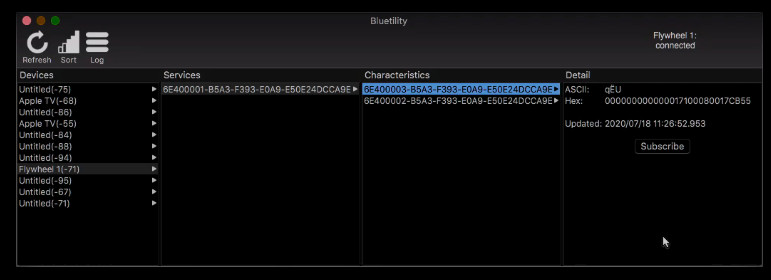
We have to admit we weren’t aware of the array of choices that the virtual biking markets offers. [ptx2] went with Zwift, which like most of these platforms, lets you pilot a smart bike through virtual landscapes along with the avatars of hundreds of other virtual riders. A little Bluetooth snooping with Bluetility let [ptx2] identify the bytes in the Flywheel bike’s packets encoding both the rider’s cadence and the power exerted, which Zwift would need, along with the current resistance setting of the magnetic brake.
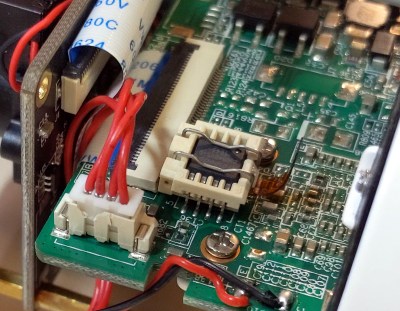
Integration into Zwift was a matter of emulating one of the smart bikes already supported by the program. This required some hacking on the Cycling Power Service, a Bluetooth service that Zwift uses to talk to the bike. The final configuration has a Raspberry Pi Zero W between the Flywheel bike and the Zwift app, and has logged about 2,000 miles of daily use. It still needs a motor to control the resistance along the virtual hills and valleys, but that’s a job for another day.
Hats off to [ptx2] for salvaging a $2,000 bike for the price of a Pi and some quality hacking time, and for sticking it to The Man a bit. We have to say that most bike hacks we see around here have to do with making less work for the rider, not more. This project was a refreshing change.
[Featured images: Zwift, Flywheel Sports]
[via r/gadgets]