The mechanical keyboard rabbit hole is a deep one, and can swallow up as much money and time as you want to spend. If you’ve become spoiled on the touch and responsiveness of a Cherry MX or other mechanical switch, you might even start putting them on other user interfaces as well, such as this Logitech joystick that now sports a few very usable mechanical keys for the touch-conscious among us.
The Logitech Extreme 3D Pro that [ErkHal] and friend [HeKeKe] modified to accept the mechanical keys originally had a set of input buttons on the side, but these were unreliable and error-prone with a very long, inconsistent push. Soldering some mechanical switches directly on the existing board was a nice improvement, but the pair decided that they could do even better and rolled out an entire custom PCB to mount the keys more ergonomically. The switches are Kailh Choc V2 Browns and seem to have done a great job of improving the responsiveness of the joystick’s side buttons. If you want to spin up your own version, they’ve made the PCBs available on their GitHub page.
While [ErkHal] notes the switches aren’t the best and were only used since they were available, they certainly appear to work much better than what the joystick shipped with originally. In fact, we recently saw similar switches used to make a custom mechanical keyboard made for the PinePhone.





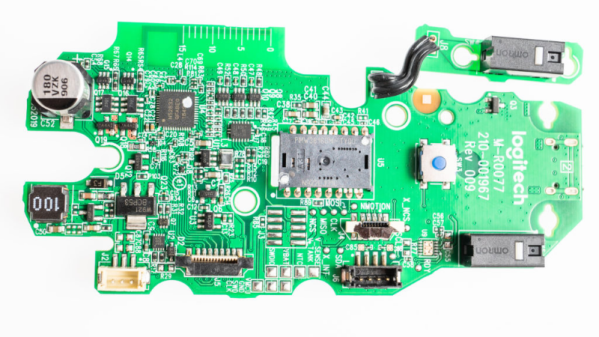
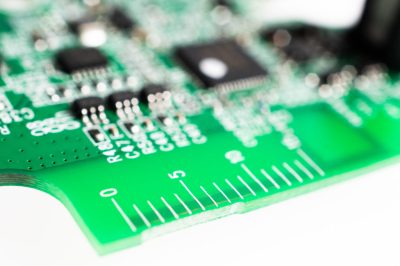 [Eric] points out several incremental changes in design which have resulted in improved ergonomics. He also uncovers a few nuggets of useful information. The use of interchangeable mold inserts help make molds last longer while still offering the flexibility to make changes in the molded part. It’s interesting to see special components being used for withstanding vibration and high-G forces. Some of these insights can be useful for those moving from prototyping to production. There’s one puzzling feature on the new PCB that [Eric] cannot figure out. There is a 15 mm scale screen-printed over the blue tooth antenna. If you have an answer on its purpose, let us know in the comments below.
[Eric] points out several incremental changes in design which have resulted in improved ergonomics. He also uncovers a few nuggets of useful information. The use of interchangeable mold inserts help make molds last longer while still offering the flexibility to make changes in the molded part. It’s interesting to see special components being used for withstanding vibration and high-G forces. Some of these insights can be useful for those moving from prototyping to production. There’s one puzzling feature on the new PCB that [Eric] cannot figure out. There is a 15 mm scale screen-printed over the blue tooth antenna. If you have an answer on its purpose, let us know in the comments below.