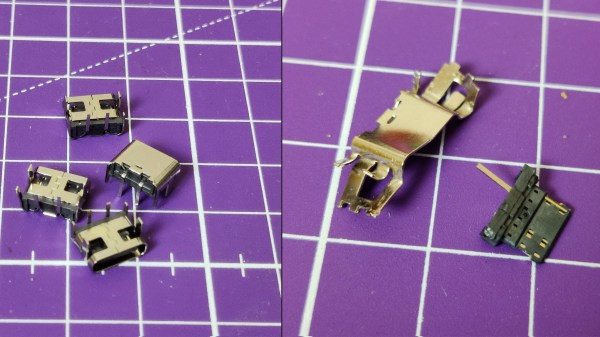
People don’t usually go as far as [Wenting Zhang] has – designing a new IDE SSD board for a portable x86 computer made in 2006. That said, it’s been jaw-dropping to witness the astounding amount of reverse-engineering and design effort being handwaved away.
The Benq S6 is a small MID (Miniaturized Internet Device) with an Atom CPU, an x86 machine in all but looks. Its non-standard SSD’s two gigabytes of storage, however, heavily limit the OS choice – Windows XP would hardly fit on there, and while a small Linux distro could manage better, it’s, and we quote, “not as exciting”. A lot of people would stop there and use an external drive, or a stack of adapters necessitating unsightly modifications to the case – [Wenting] went further and broke the “stack of adapters” stereotype into shards with his design journey.
 Tracing quite a few complex multi-layer boards into a unified and working schematic is no mean feat, especially with the SSD PCB being a host to two BGA chips, and given the sheer amount of pins in the IDE interface of the laptop’s original drive. Even the requirement for the SSD to be initialized didn’t stop him – a short fight with the manufacturer’s software ensued, but was no match for [Wenting]’s skills. The end result is a drop-in replacement SSD even thinner than the stock one.
Tracing quite a few complex multi-layer boards into a unified and working schematic is no mean feat, especially with the SSD PCB being a host to two BGA chips, and given the sheer amount of pins in the IDE interface of the laptop’s original drive. Even the requirement for the SSD to be initialized didn’t stop him – a short fight with the manufacturer’s software ensued, but was no match for [Wenting]’s skills. The end result is a drop-in replacement SSD even thinner than the stock one.
This project is well-documented for all of us to learn from! Source code and PCB files are on GitHub, and [Wenting] has covered the journey in three different places at once – on Hackaday.io, in a YouTube video embedded down below, and also on his Twitter in form of regular posts. Now, having seen this happen, we all have one less excuse to take up a project seemingly so complex.
Hackers play with SSD upgrades and repurposing every now and then, sometimes designing proprietary-to-SATA adapters, and sometimes reusing custom SSD modules we’ve managed to get a stack of. If case mods are acceptable to you aesthetics-wise, we’ve seen an SSD upgrade for a Surface Pro 3 made possible that way.
Continue reading “Custom SSD Gives New Life To Handheld Atom PC”