According to researchers at GTSC, there’s an unpatched 0-day being used in-the-wild to exploit fully patched Microsoft Exchange servers. When they found one compromised server, they made the report to Microsoft through ZDI, but upon finding multiple Exchange servers compromised, they’re sounding the alarm for everyone. It looks like it’s an attack similar to ProxyShell, in that it uses the auto-discover endpoint as a starting point. They suspect it’s a Chinese group that’s using the exploit, based on some of the indicators found in the webshell that gets installed.
There is a temporary mitigation, adding a URL-based request block on the string .*autodiscover\.json.*\@.*Powershell.. The exact details are available in the post. If you’re running Exchange with IIS, this should probably get added to your system right now. Next, use either the automated tool, or run the PowerShell one-liner to detect compromise: Get-ChildItem -Recurse -Path -Filter "*.log" | Select-String -Pattern 'powershell.*autodiscover\.json.*\@.*200. This one has the potential to be another really nasty problem, and may be wormable. As of the time of writing, this is an outstanding, unpatched problem in Microsoft Exchange. Come back and finish the rest of this article after you’ve safed up your systems.






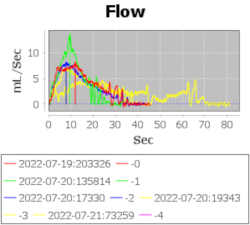 For the hardware, [Jerry] took a small digital scale of a certain model and reused its load cell-based weighing mechanism using an HX711 amplifier, replacing the screen and adding an extra box for control electronics. With an Arduino MKR1010 as brains of the operation, the hardware’s there to log flow data, initially recorded onto the SD card, with WiFi connectivity to transfer the data to a computer for plotting; a DS3234 RTC breakout helps keep track of the time, and a custom PCB ties all of these together. All of these things are easy to put together, in no small part due to the extensive instructions provided.
For the hardware, [Jerry] took a small digital scale of a certain model and reused its load cell-based weighing mechanism using an HX711 amplifier, replacing the screen and adding an extra box for control electronics. With an Arduino MKR1010 as brains of the operation, the hardware’s there to log flow data, initially recorded onto the SD card, with WiFi connectivity to transfer the data to a computer for plotting; a DS3234 RTC breakout helps keep track of the time, and a custom PCB ties all of these together. All of these things are easy to put together, in no small part due to the extensive instructions provided.










